PRODUCT DESCRIPTION
Automated Incident Response Platform
The ActiveCanopy platform cuts through the security noise and quickly adapts to find the unknown threats, enabling efficient detection and response.
See how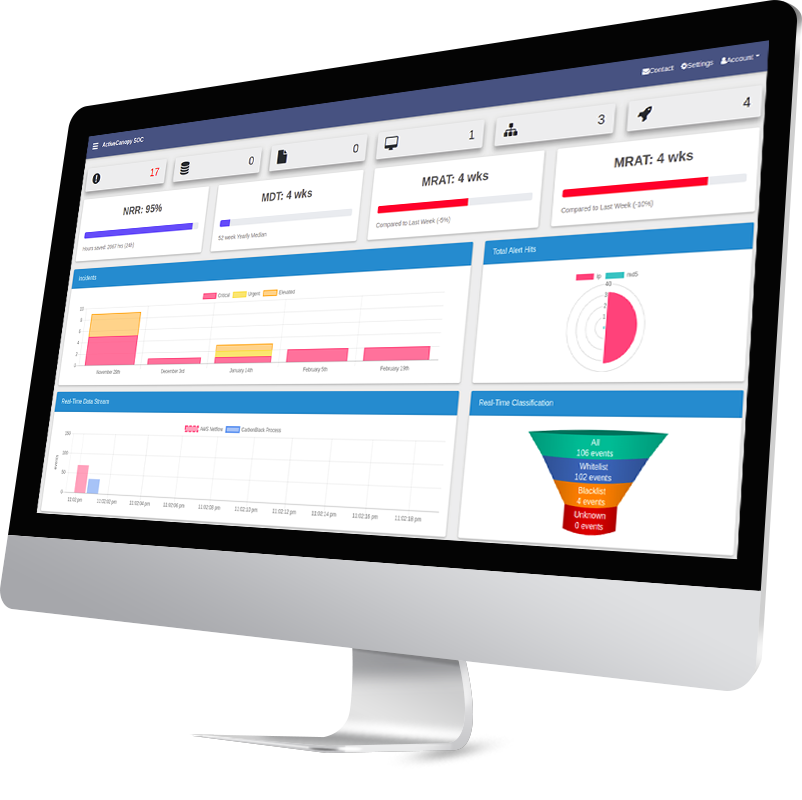
How it works
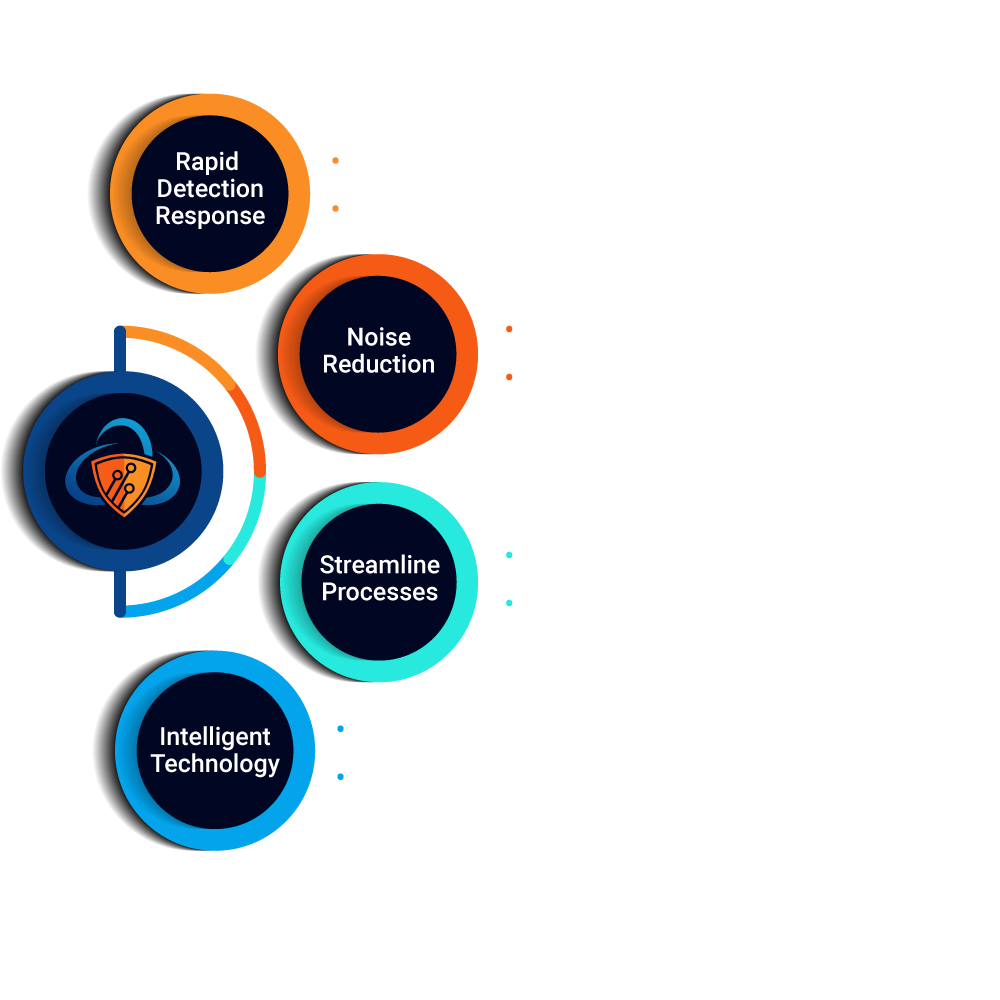
The platform quickly aggregates ingested data, prioritizing and elevating threats for immediate analysis. This unique capability allows for the discovery of known and unknown threats for rapid detection and response.
The platform provides an automated enrichment capability that adds context to data security telemetry aiding analysts to identify patterns and relationships for focused deep dive analysis and reporting.
The platform applies a heuristic algorithm for noise reduction that filters events resulting in extreme data clarity and optimal labeling for threat hunting. Eliminating wasting resources on investigating non malicious datasets.
The platform encapsulates intelligent technology of machine learning algorithms for a continuous feedback loop to reprioritize and automatically tune the system baseline for anomaly discovery and predictive analytics.
PRODUCT SUBSCRIPTIONS
ActiveCanopy Tiers
ActiveCanopy allows complete flexibility in infrastructure deployment. Protect your organization from advanced security threats, gain greater security control, enhance productivity with any solution that fits your needs.
Community
- Limited On Demand Automations
- Limited Incident History
- Incident Report
- Limited Technical Support
- Limited User Role
- Single-Tenant
- Open Source Connectors
- Machine Learning
Enterprise
- Unlimited Automations
- Unlimited Incident History
- Enterprise Reports Package
- 24/7 Technical Support
- Multi-User Roles
- Single/Multi-Tenant
- Open Source Connectors
- Commercial Connectors
- Machine Learning
MSSP
- Unlimited Client Engagements
- Unlimited Incident History
- Enterprise Reports Package
- 24/7 Technical Support
- Multi-User Roles
- Multi-Tenant
- Multi-Customer
- Open Source Connectors
- Commercial Connectors
- Machine Learning across Market Sectors
Streamlined Product Workflow
Allows users the ability to manage, respond and
remediate all cybersecurity incidents.
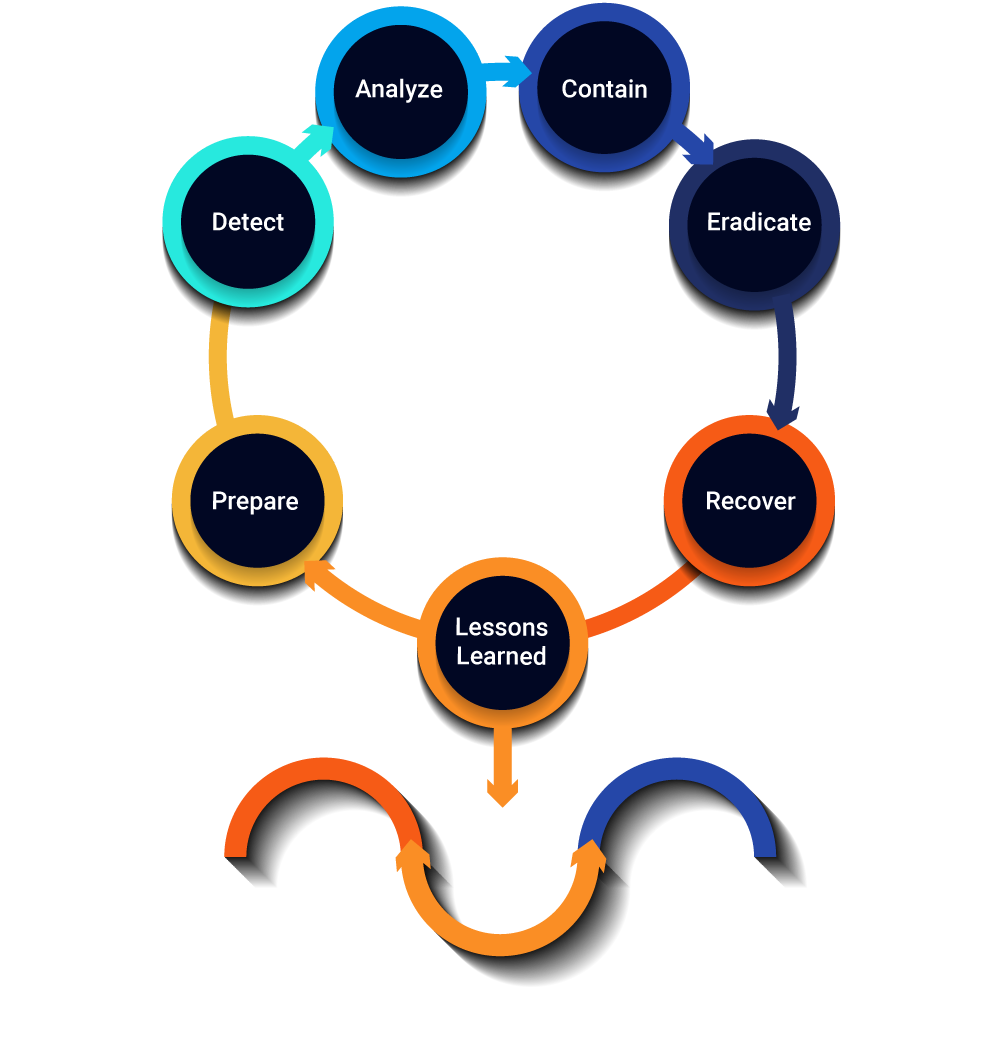
Reduce threat detection and response time though automated detection and alert notifications.
Intuitive user interface dashboard enables detailed analysis streamlining queries, task and ticketing.
Ability to gather, analyze and prioritize crucial data at the click of a button, further enhancing the threat detection and incident management process.
Greater level of visibility and enhanced oversight into the entire cyber security process.
Managed Services
At ActiveCanopy we offer fully managed security support. Our experts will become part of your security team, as we monitor and protect your organization, and optimize your security resources.
Need HelpIncident Response
Our technical response team of cyber threat analysts, forensic specialists, and reverse engineers, will investigate, contain, and remediate any security incident with speed to minimize disruption.
Cyber Threat Reports
Our cyber intelligence analysts will tailor industry specific reports providing insight into the threat landscape that can impact your business operations.
Security Assessment
Our experienced assessors will identify your organization's cyber risk through a vulnerability assessment, penetration test, or compliance review.
Dark Web Analytics
Our research experts monitor cyber crime marketplaces and forums to locate your compromised data.
Why ActiveCanopy
They Trust Us
Cyber Hunter Blog
Contact

ActiveCanopy has the best in the business cyber domain expertise providing cutting-edge technology developed by pioneering security experts.
Contact Us
Request a demo: [email protected]
Support: [email protected]
General Inquiries: [email protected]
Phone Number: 1-800-504-2130
Corporate Headquarters
11921 Freedom Dr., Ste. 550, Reston, VA 20190
Texas Office
18911 Hardy Oak Blvd, Ste. 110, San Antonio, TX 78258